New Feature Release: Streamline User Access Reviews with Hyperproof
At Hyperproof, we recognize the growing demand for precision and efficiency in User Access Reviews (UAR) within the governance, risk, and compliance (GRC) landscape. Traditional manual processes are cumbersome and error-prone, exposing critical security gaps.
Our new UAR feature automates and simplifies UAR workflows, helping organizations swiftly identify and address access discrepancies. This enhances overall system security and reduces the risk of breaches.
What are user access reviews?
User Access Reviews (UAR) are periodic checks to ensure users have appropriate access rights, reducing security risks and ensuring compliance with regulations. Effective user access reviews are indispensable for preventing data breaches, unauthorized access, and other costly security incidents, preserving the integrity and trustworthiness of your organization’s information security framework.
The challenges of outdated access management
In the past, user access reviews were done manually across multiple disparate systems. This outdated process comes with several pain points:
Time-consuming manual processes
Reviews are typically done quarterly, and each cycle can require hundreds of manual tasks, adding hundreds of hours of effort. Many organizations have to allocate substantial resources, including full-time employees, just to keep up with the workload.
Disjointed systems
Managing user access across multiple platforms often means working with a variety of tools — spreadsheets, emails, and ticketing systems — that don’t integrate, resulting in delays and inefficiencies.
Lack of real-time information
Organizations struggle with delayed or outdated data, which can lead to potential security gaps and complicate the audit process.
The Hyperproof advantage
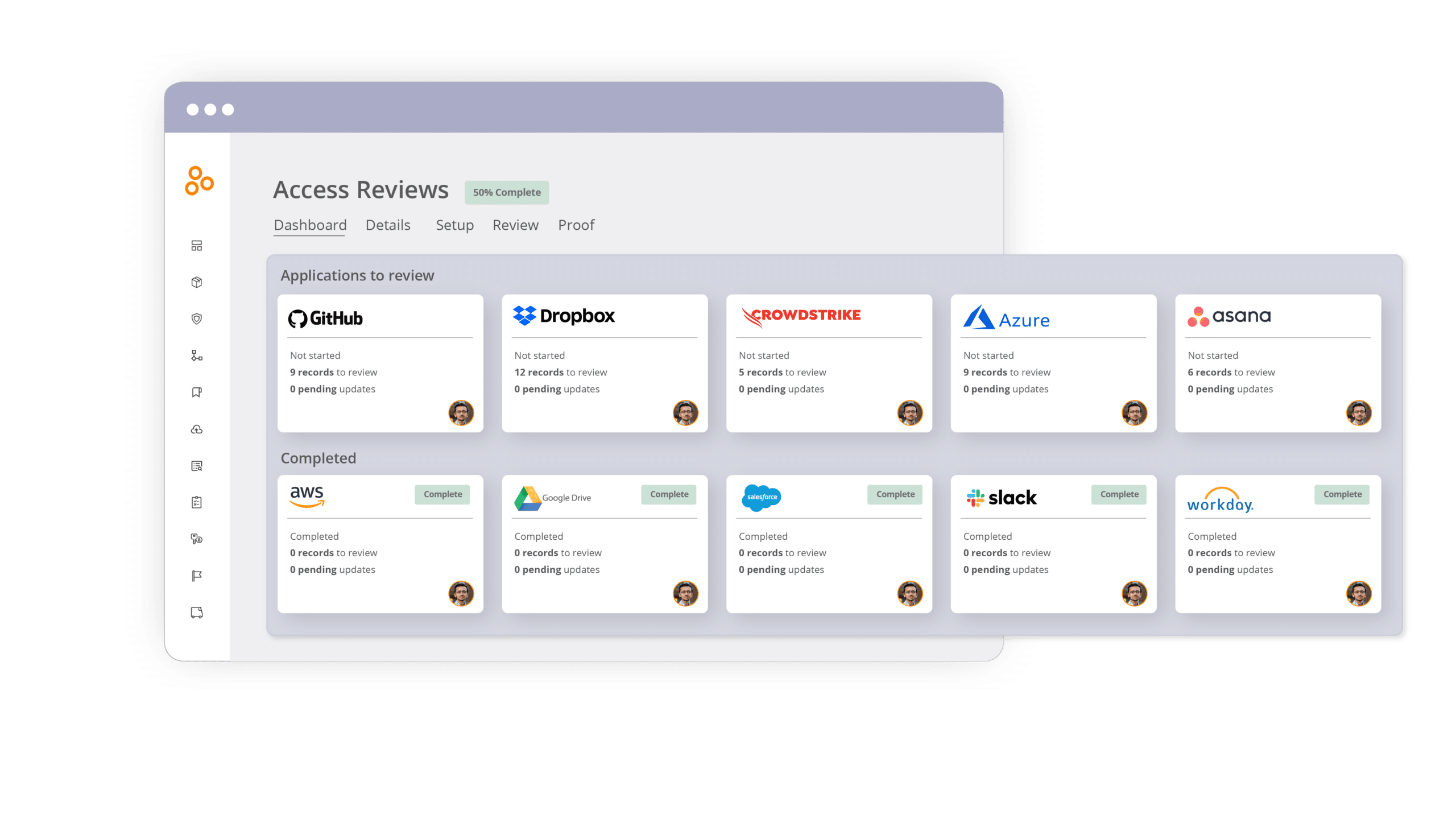
Hyperproof’s new User Access Reviews module solves these challenges by providing a comprehensive workflow that simplifies user access management, integrates seamlessly with major platforms, and offers real-time insights into access review processes.
1. Security and compliance
Protecting sensitive information is more critical than ever. Hyperproof ensures that only authorized personnel have access to review sensitive data. Additionally, access reviews are linked to controls to ensure accuracy and audit preparedness.
2. Efficiency through integration
Hyperproof integrates with leading HRIS providers, AWS, Azure, Google, and Okta, unlocking hundreds of integrations. This enables organizations to pull user access information from multiple systems and manage permissions from one platform. Instead of juggling various tools, Hyperproof centralizes access review management, cutting down the time and effort required for audits.
3. Simplicity and ease-of-use
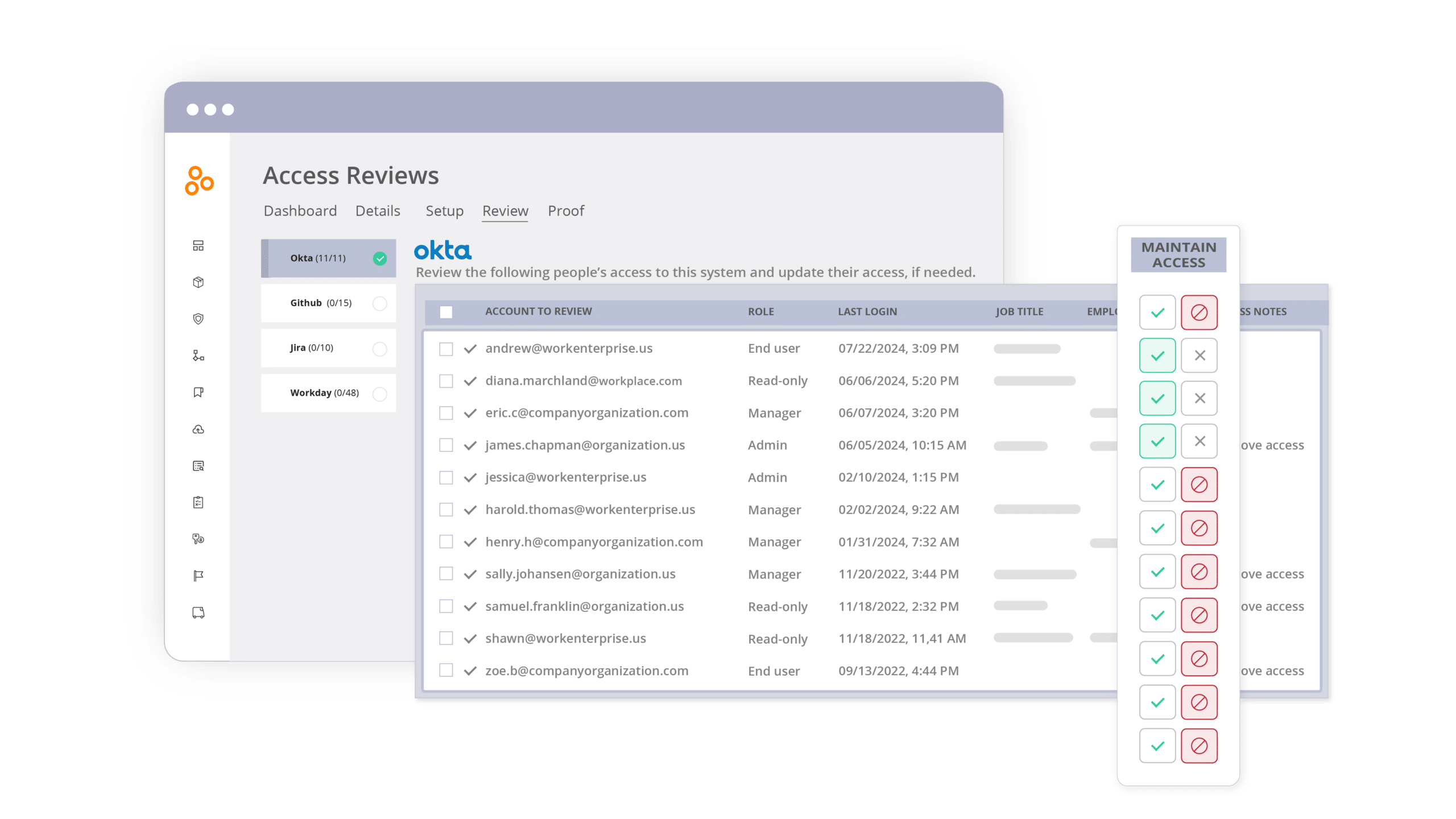
Hyperproof’s intuitive user interface minimizes the need for extensive training, allowing team leaders to quickly review, adjust, and verify access permissions. Hyperproof also allows users to notify reviewers over email or their favorite task management platform.
4. Real-time insights
With real-time status updates, Hyperproof helps identify areas that need attention immediately, streamlining the entire access review process. Robust reporting also ensures transparency and provides the necessary audit evidence, reducing the complexities of audit preparation.
Protect your data and streamline your resources
In a landscape where data breaches are becoming more common and regulatory requirements are more stringent, organizations need a reliable solution for managing user access. Hyperproof’s User Access Reviews module offers an intuitive, integrated, and efficient approach to user access reviews, helping organizations secure sensitive data while optimizing their team’s resources.
By leveraging Hyperproof’s User Access Reviews module, companies can stay ahead of potential threats, meet compliance requirements, and free up their teams to focus on more strategic tasks. If you’re looking to modernize your access review process, Hyperproof is here to help.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












